Intelligence at the edge is in many cases an “unmissable” architecture requirement in today’s IoT type product. Some markets and verticals highlight the importance of this requirement driven by performance, compliance & licensing, scalability and security.
Latest market opening driven by 5G even push this requirement to get:
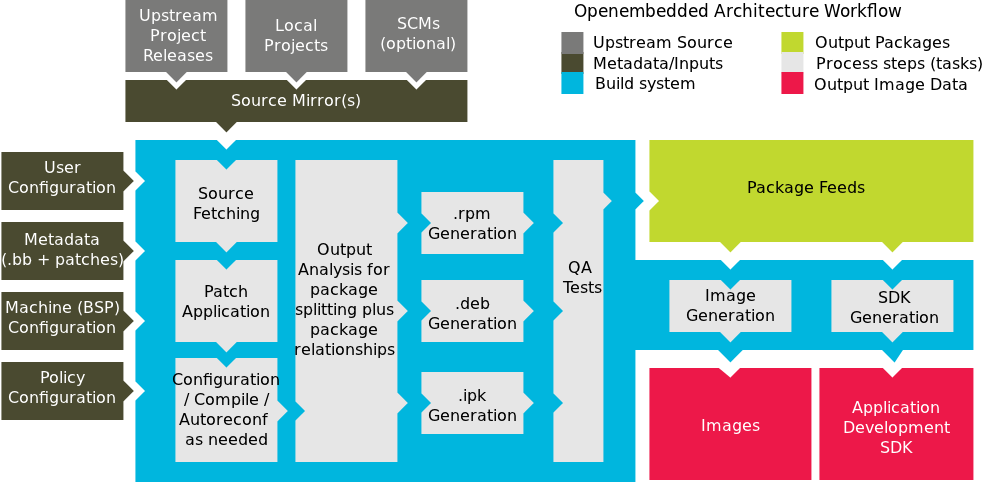 Source: yoctoproject.org
Since the last 2-3 years, Wind River maintains a serious distro giving a new level of maturity oriented on:
Source: yoctoproject.org
Since the last 2-3 years, Wind River maintains a serious distro giving a new level of maturity oriented on:
- More CPU power to the edge (autonomous driving, assisted tele-medical device, Advanced IoT)
- More connectivity (protocol stack, encryption, commissioning)
- More complex processing requiring complex software modules (multifactor identification, dynamic authentication)
 Source: yoctoproject.org
Since the last 2-3 years, Wind River maintains a serious distro giving a new level of maturity oriented on:
Source: yoctoproject.org
Since the last 2-3 years, Wind River maintains a serious distro giving a new level of maturity oriented on:
- Security (security patch, vulnerability testing and protection mechanism)
- Compliance (licensing)
- Performance (Real Time, hardware real time build switch)
- Open Source Software Compliance Artifacts
- Security Vulnerability Protection
- Support and Maintenance
- Authentication to ensure that any module running is keyed
- From developer commit verification, making sure any source is not tampered
- Bake kernel image
- Wind River Linux – Open Source Leadership: https://windriver.com/products/linux/
- The Yocto project: https://www.yoctoproject.org/
- Amotus and Dimonoff Open Source Project Contributions: https://amotus.com/resources/contribution-to-open-source-projects/
- Making the Grade with Cybersecurity, Linux, and the Intelligent Edge: https://resources.windriver.com/linux/making-the-grade-with-cybersecurity-linux-and-the-intelligent-edge
- GitHub Contributions (Wind River Labs): https://github.com/WindRiver-Labs/wrlinux-x
- Common Vulnerabilities and Exposures: https://en.wikipedia.org/wiki/Common_Vulnerabilities_and_Exposures

You have an idea for a project and need our expertise to achieve it?
Contact our experts!






